Social media sites are a near-bottomless source of information that almost anyone can use for security and intelligence research, as well as for marketing campaigns. The platforms allow anybody to learn more about other people, their interests, experiences and affiliations, while organizations can easily scour the sites to gain insights about customer sentiment or to predict consumer behavior.
It’s little wonder then that techniques such as Open Source Intelligence (OSINT) are increasingly popular. These days, there are numerous tools that automate the collection and analysis of public data about internet users. These techniques are also applied specifically for social media intelligence, sometimes called SOCMINT.
In this article, we’ll look at several tools that may aid your social media intelligence efforts. Importantly, they are also a testament to the importance of being wary of what kind of information any of us shares online.
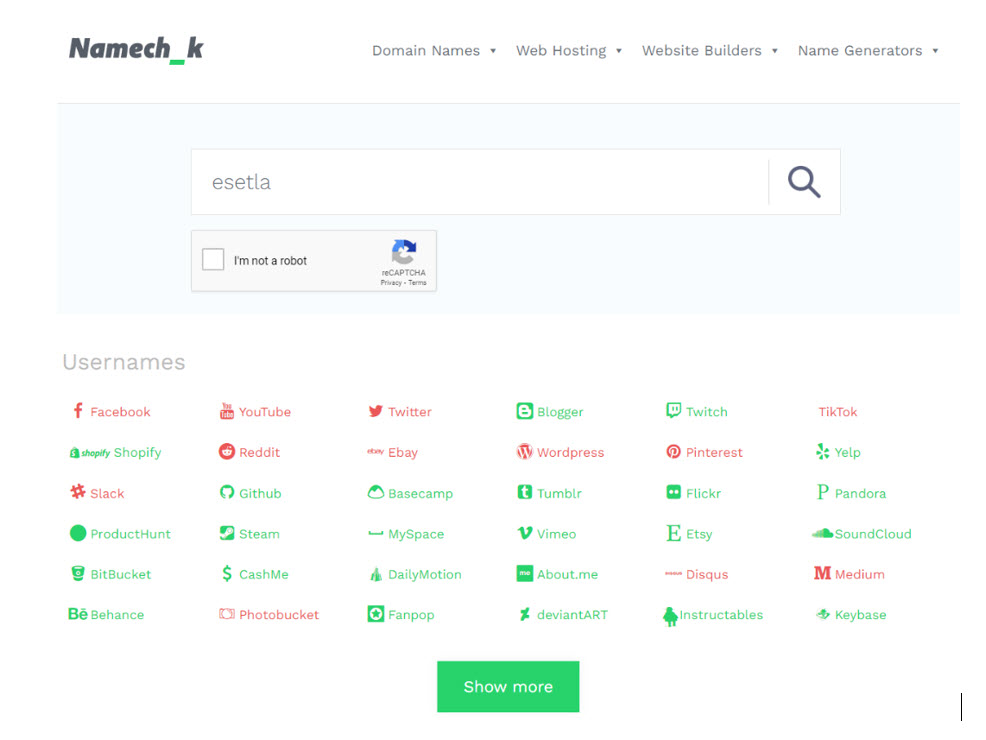
Namechk
Let’s start with the easiest one. In addition to checking the availability of a username on various online platforms, Namechk lets you easily search for a person’s online personas. To do this, just enter a username and Namechk will comb through multiple online platforms to find user profiles that match the information provided. This is useful for researchers, journalists, businesses and government agencies looking to collect online information about a person or for people looking to reconnect with long-lost friends or acquaintances.
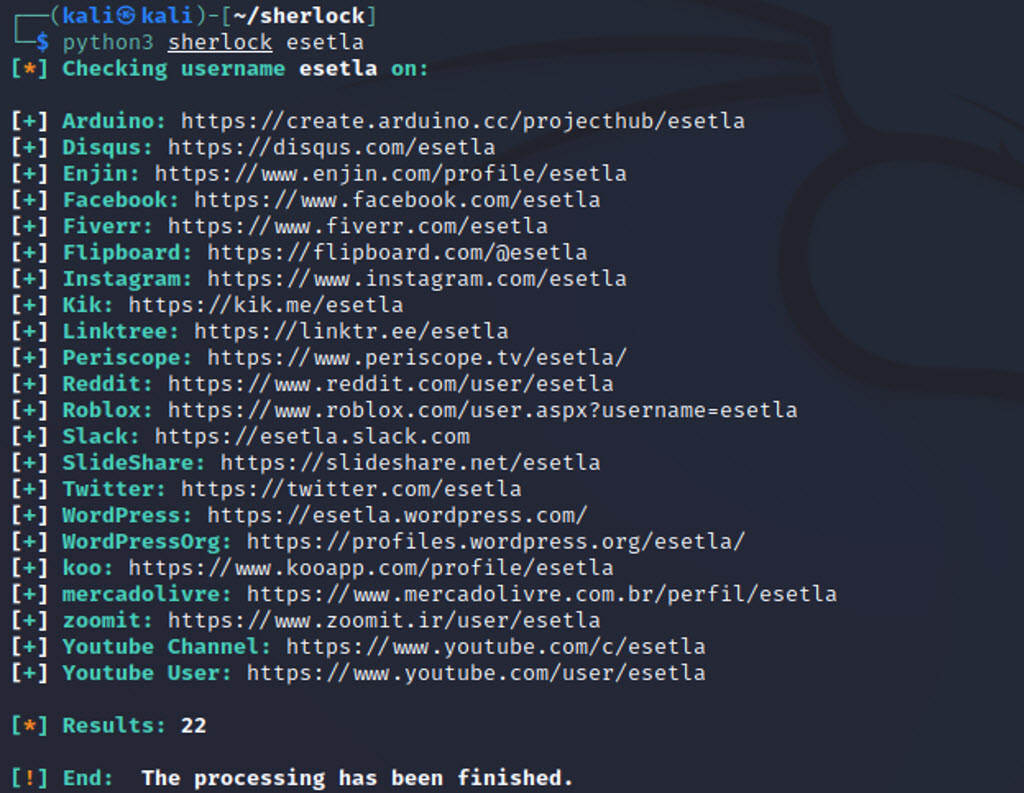
Sherlock
Sherlock is an open-source, command-line tool developed in Python that, much like Namechk, searches for a particular username on the most popular social networks before spitting out links to the profiles. It has no interface and is accessed via a Windows, Linux or MacOS command terminal. For more information and installation guidance, check out the GitHub repository of the Sherlock Project.
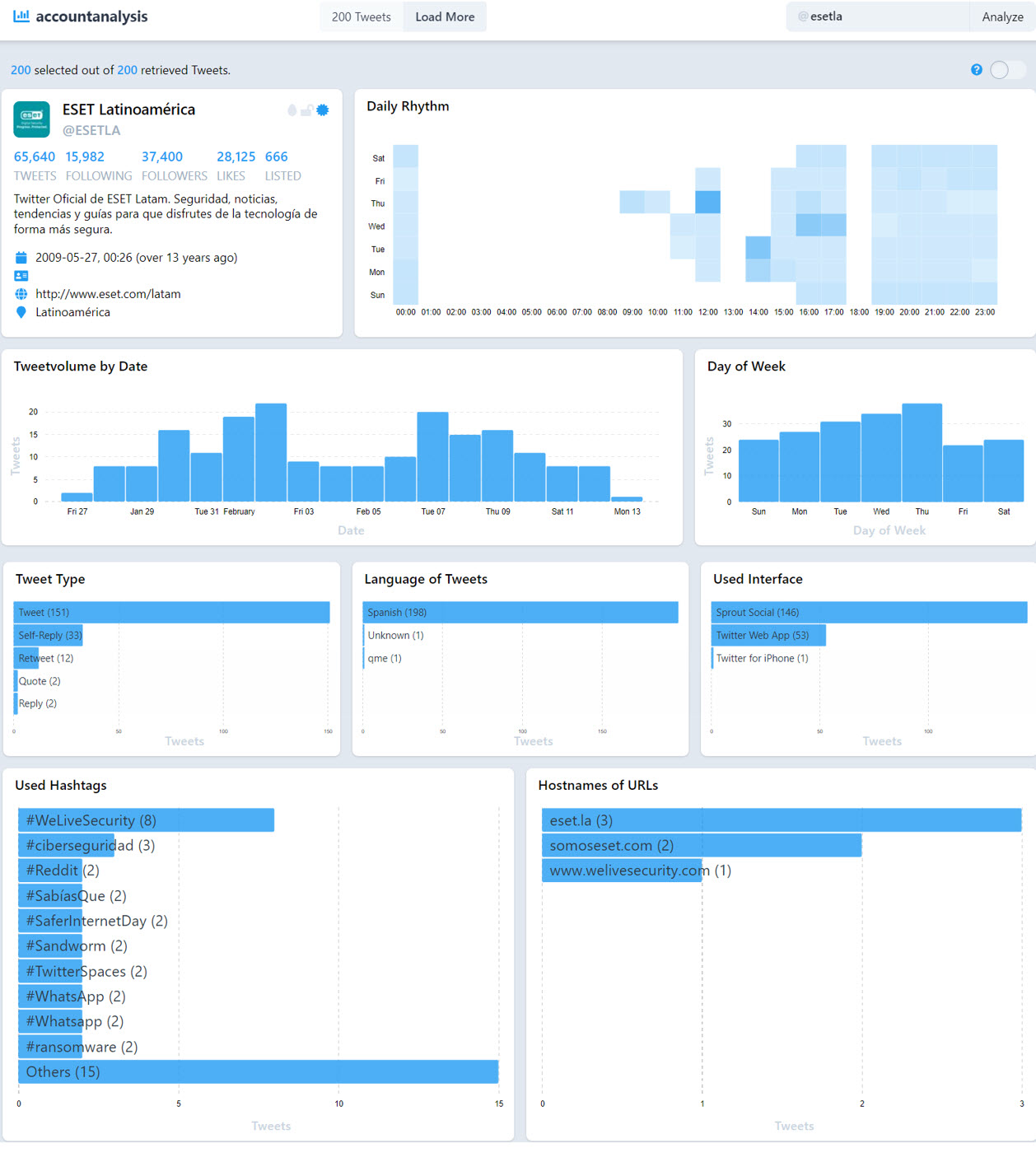
accountanalysis
accountanalysis is used to perform OSINT research with a focus on Twitter. It produces a report that is a bird’s eye view of an account’s public information, including its followers and followed accounts, frequency of tweets, number of interactions, times of greatest activity, most used hashtags and many more.
This data is useful to draw a variety of conclusions: From learning more about people’s tastes or opinions to checking whether it is an automated user or bot (e.g., based on posting schedules) to discovering accounts that have malicious purposes due to their promoting sites with a bad reputation.
Maltego
Maltego is one of the best known and most powerful tools in the OSINT world. It uses graphs to represent information, which allows you to create relationship diagrams to identify patterns and discover hidden connections. It also stands out for the number of sources it uses.
The most-used features are those that make it possible to identify and visualize relationships between what the tool calls entities, such as IP addresses, domain names, e-mails, social network users, etc. In addition, Maltego allows you to integrate different sources of information, such as databases, online search tools, APIs, etc.
When creating a new graph within the tool, we can insert entities or already-known data about the target, such as email, commonly used username or full name. And with the help of “transforms”, Maltego will add the related entities to the first one.
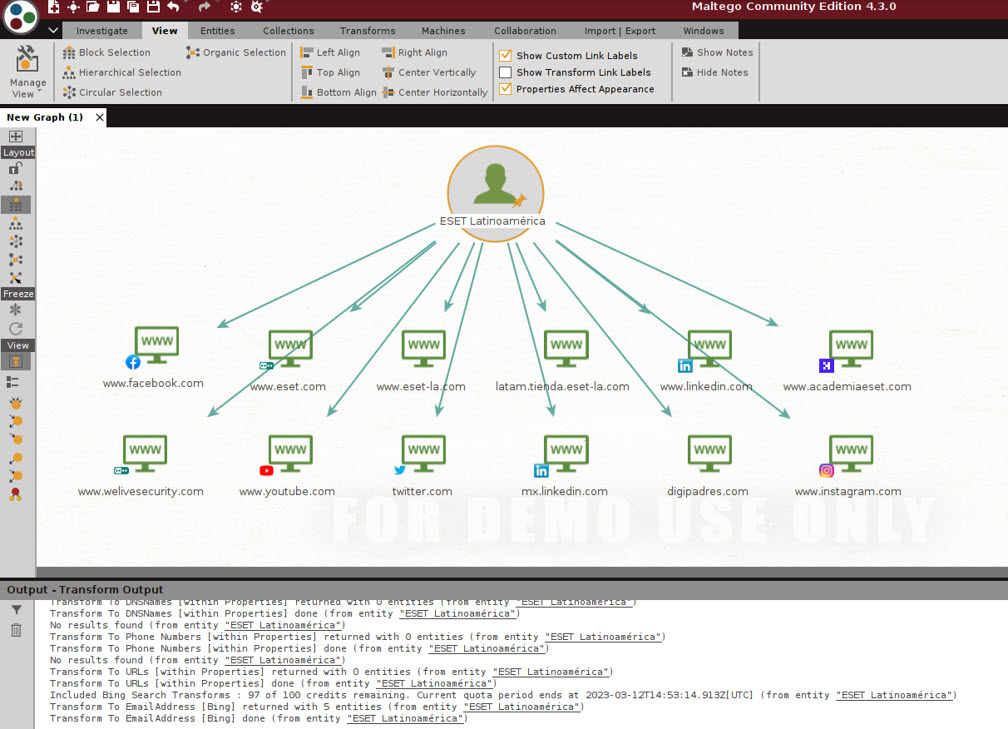
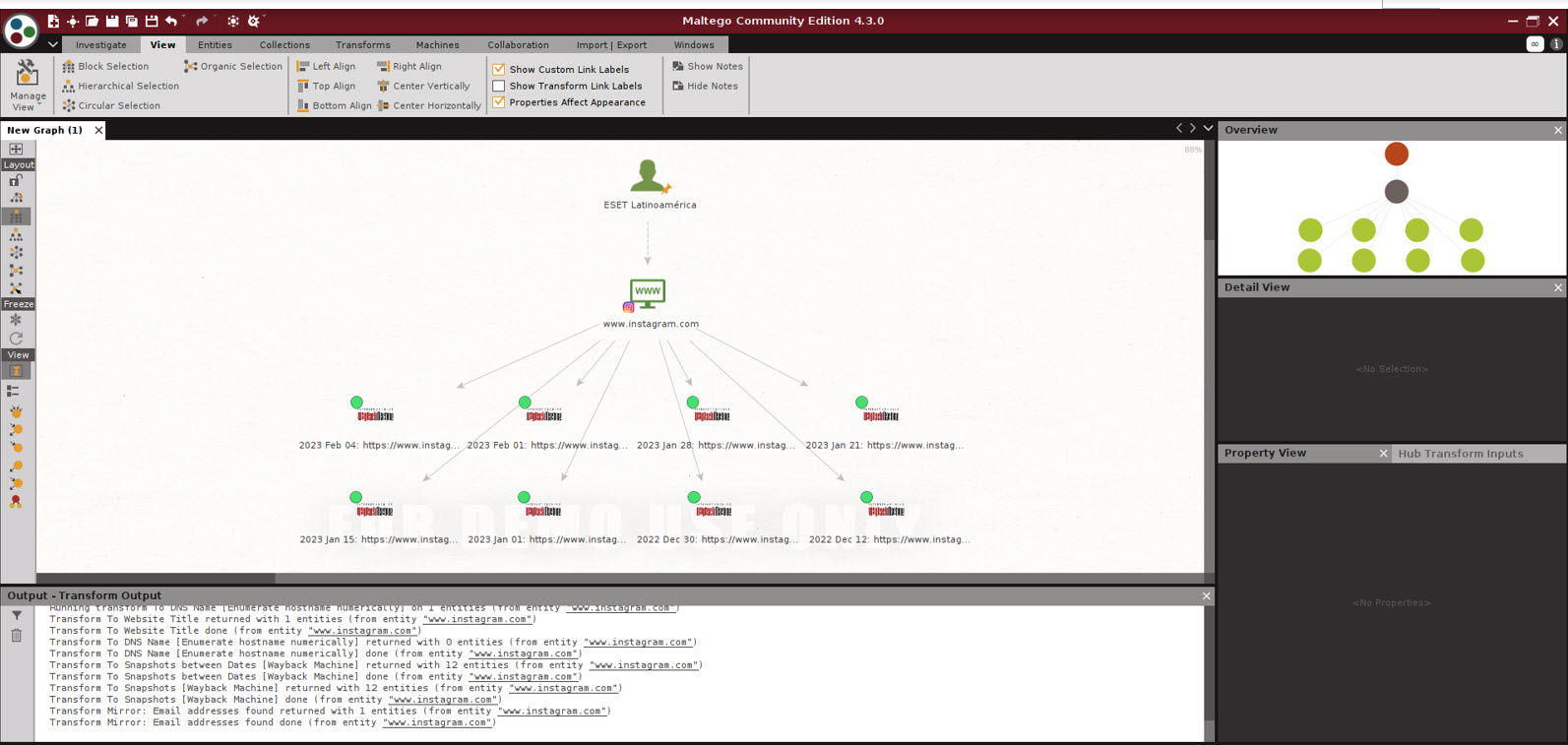
For example, in the following image we see some entities resulting from a search for “ESET Latinoamérica”. Among others, the tool returned ESET’s social networks and related sites, including WeLiveSecurity.
From the newly discovered entities, it is possible to re-run the transforms. The following image shows that digging into the resulting Instagram profile returns files saved in the Wayback Machine.
Maltego, available for download from the official site, is a desktop application that offers free (but limited) licensing and unlimited paid versions at both user and corporate levels.
Social media as search engines
Okay, this is not really what you would think of as an OSINT tool, but search functionalities that are integrated within social media sites may double as powerful resources for intel gathering – without leaving the app itself. This is especially the case if the target of your research is a close or famous person. Some useful options are:
- Profile search: Search for the full name and other relevant details of the person you are researching to find their profile on the social network and view their public activity, such as their posts and shared photos.
- Hashtag search: Use relevant hashtags to find posts related to the person you are researching. For example, if you are looking for information about an event, it is possible to search for the hashtag associated with that event and see if the person has shared information about it.
- Group search: Check if the person you are researching is a member of any groups on the social network, as this can provide additional information about their interests and activities.
- Mention search: Search for mentions of the person you are researching on the social network, to see if other people are talking about them and get more information about their online reputation and relationships.
Recommendations
When using OSINT tools, make sure to apply certain measures to ensure that the privacy and security of individuals and the information collected is respected. This is why we recommend:
- Know the law: It is crucial to know the local and national laws and regulations related to the collection and use of public information to ensure that you do not commit a crime or violate the privacy of others.
- Respect people’s privacy: It is important not to collect private or confidential information without the explicit consent of the affected person.
- Verify the information: It is important to verify the truthfulness and relevance of the collected information before using it for any purpose.
- Preserve security: When collecting and storing information, it is important to take measures to protect it against possible theft or data breaches.
OSINT tools for social media research can be very useful, but also remind us of the importance of protecting the information that we do not want to be available or that could be used for malicious purposes.
Be careful about what you post online and avoid oversharing details from your private life on social media.
RELATED READING:
Cleaning up your social media and passwords: What to trash and what to treasure
Attack of the Instagram clones
Facebook etiquette: Behaviors you should avoid
Using Discord? Don’t play down its privacy and security risks