In recent months, we have analyzed several threats that have been detected in high volumes, higher than usual in many countries such as Germany and Spain. Perhaps the most interesting case analyzed recently concerns the Nemucod malware, which was spreading Teslacrypt ransomware variants, among other threats.
In this post we are going to analyze Bayrob, another trojan that has been intensely targeting several countries since the middle of December, trying to get as many victims as possible.
Attack vector: malicious attachment in an email trying to impersonate Amazon
Like many other threats, Win32/Bayrob is distributed using a classic attack vector (for example, as a malicious attachment in an email). In several cases, the criminals behind this campaign were trying to attract their victims by posing as Amazon, but a quick check of the sender’s email address reveals that they have nothing to do with this company:
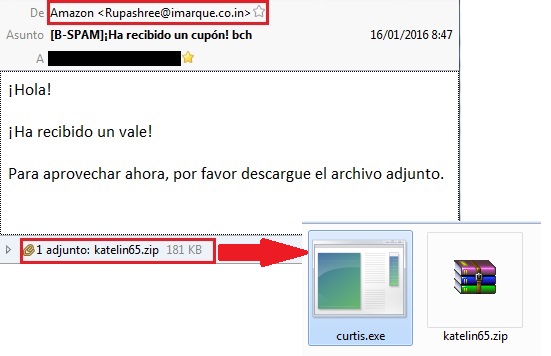
We can also see that the attached ZIP file contains an executable. That’s the malware file, and if we run it, it will start to take malicious actions on our system while showing the following error message to make the victim believe that he downloaded a file that can’t be used on his system.
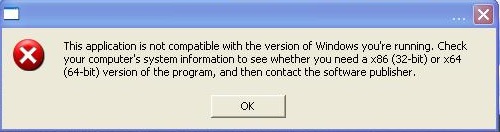
But the reality it’s quite different, since the malware is already loaded on the victim’s system and the attackers could be using it as a backdoor. This trojan registers itself as a system service and can also modify the system registry to make sure that it will be executed on every system restart.
One of the goals of this trojan is to steal information from the victim’s computer. Among the information that’s stolen and sent to a remote server we can see:
- Operating system version
- Computer Name
- Computer IP Address
- Information about the operating system and system settings
- MAC address
- List of running services
Of course, this kind of information is not the main target of the attackers, since they are eventually hoping to obtain more critical data such as credit card information and online banking credentials. To do that, this trojan is able to communicate, using the HTTP protocol, with a remote computer controlled by the attackers and perform the following operations:
- Download malicious files from a remote computer
- Run executable files
- Send the list of running processes to a remote computer
- Send gathered information
- Update itself to a newer version
Another interesting feature of this trojan is that it can generate various URLs in addition to the one used to contact the remote computer controlled by the attackers. In this case, for example, here is how the malware uses three different URLs:
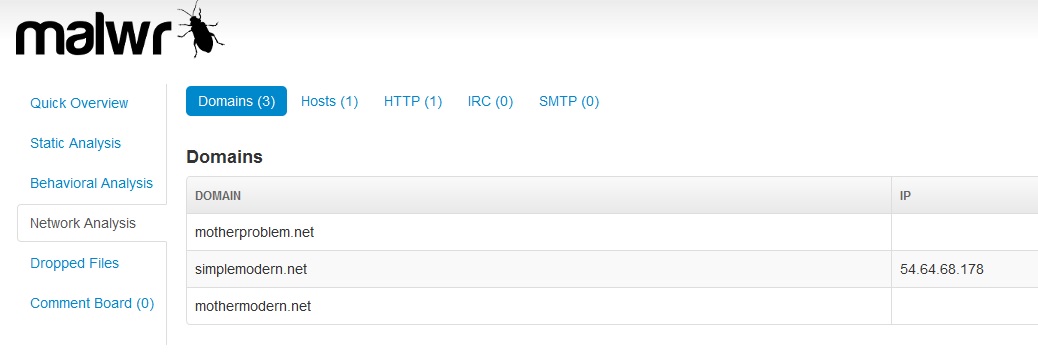
The URL “simplemodern.net” is registered to Amazon Japan, as shown in the following whois info, while the other two are unrelated to Amazon domains. This could be related to the fact that the attackers might be using a rented server to control and send commands to the infected machines that belongs to the Amazon Web Services infrastructure.
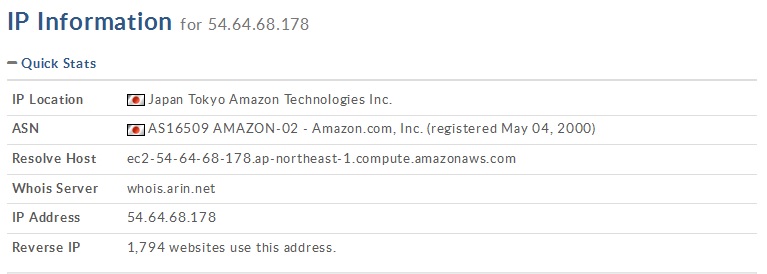
However, this doesn’t mean that any Amazon server has been compromised. It’s just that the criminals behind this campaign are using (and paying for) an existing web service infrastructure provided by Amazon Japan. This can also allow law enforcement units to contact Amazon, ask them to deactivate the server and, maybe, get some information regarding the customer who purchased the web service that may lead to the criminals.
Worldwide impact of Win32/Bayrob
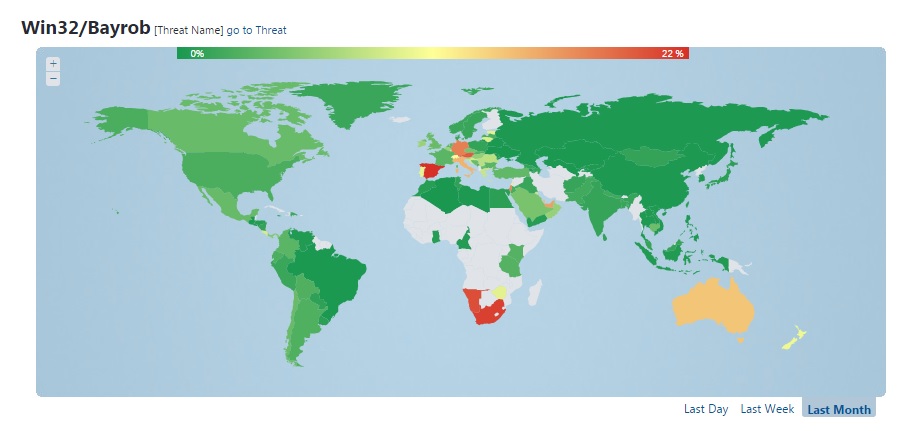
As with other recent threats seen prior to Win32/Bayrob, the impact of this malware is different depending on where in the world we are looking. In this case, the attackers have focused mainly on Europe, South Africa, Australia and New Zealand.
Two of the countries most affected are Germany and Spain. If we look at the Virus Radar statistics during the period of time that goes from mid-December until mid-January, Bayrob was the most detected malware, with detection rates above 15% in these two countries, and significant rates in other countries as well.
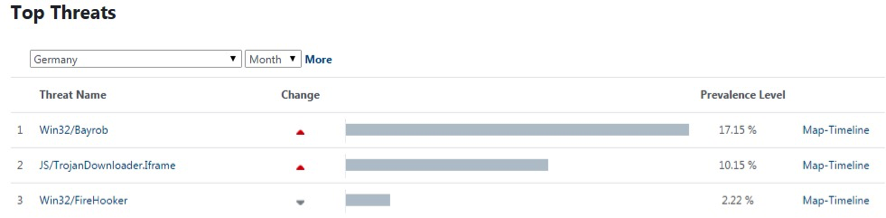
Top Malware Threats for Germany, December 2015 – January 2016
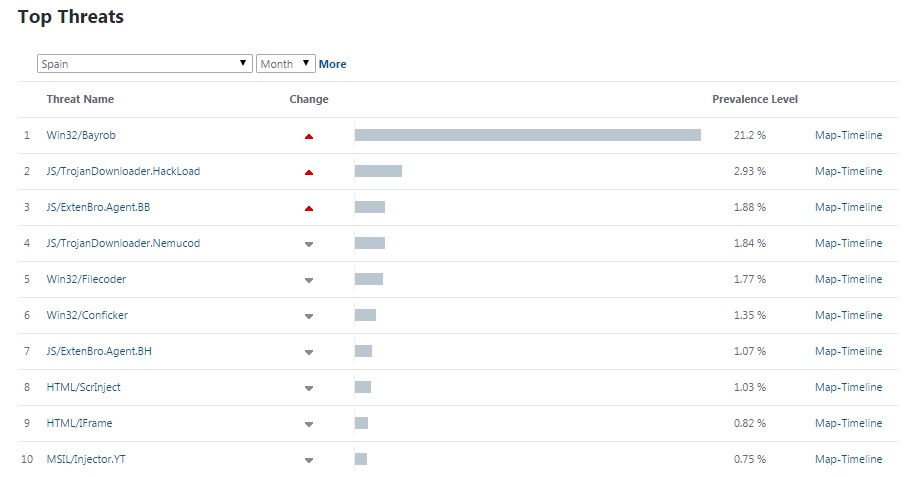
Top Malware Threats for Spain, December 2015 – January 2016
In fact, previous variants of the Win32/Bayrob trojan weren't as widely reported as those that began to spread in December, as the following graphic shows:
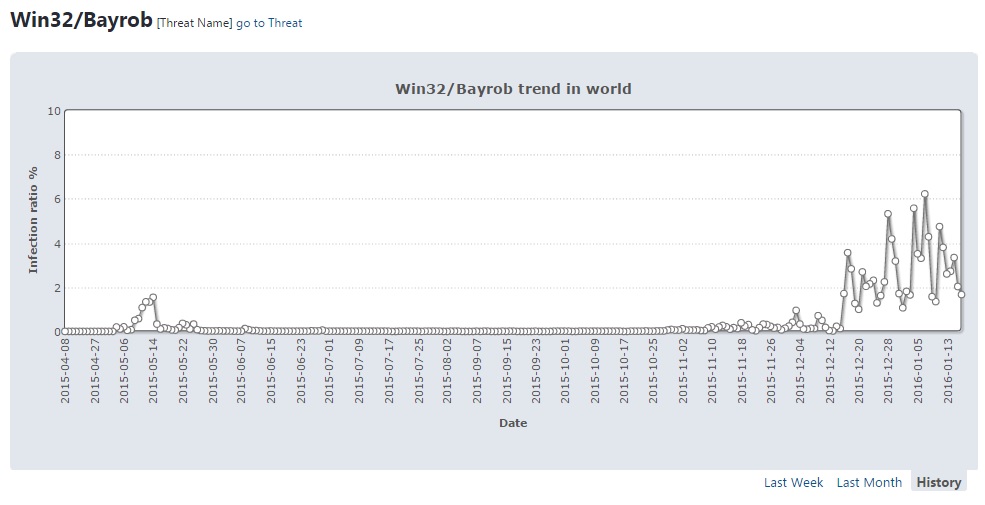
The following maps shows that detection rates weren't as high in North and South America, Asia, and most parts of Africa as in the other regions. This is quite strange since we detected malicious Bayrob emails in several languages, but this could also be a tactic used by the attackers to focus on particular countries each time.
Conclusion
These types of malware campaigns, which have a significant impact in a number of countries for a concentrated period of time, are becoming more and more common. This could mean a new strategy that focuses on affecting some markets of particular interest instead of trying to attract as many victims as possible.
However, as the method used to spread this type of malware is very well-known, we should put more effort into raising awareness among users so they can recognize such attacks easily and avoid opening malicious attachments like the one we’ve just analyzed.




