ESET has collaborated with Microsoft, CERT.PL and various law enforcement bodies around the world to disrupt known Dorkbot botnets by sinkholing their C&C servers. ESET shared technical analysis, statistical information about the malware used, and known command and control servers’ domains and IPs. We also were able to leverage our historical knowledge of this threat as we have been monitoring it and protecting our users from it for a long time, as you can see by reading ESET's Pablo Ramos’s VirusBulletin paper, which he presented in Dallas in 2012.
As a result of this effort, law enforcement agencies from around the globe, aided by Microsoft security researchers, today announced the disruption of one of the most widely distributed malware families – Win32/Dorkbot – which has infected numerous PCs in more than 190 ccountries.
Dorkbot, an IRC botnet
Win32/Dorkbot is distributed via various channels such as social networks, spam, removable media and exploit kits. Once installed on the machine, it will try to disrupt the normal operation of security software by blocking access to their update servers and will then connect to an IRC server to receive further commands.
Besides being a password stealer, targeting popular services such as Facebook and Twitter, Dorkbot typically installs code from one of several other malware families soon after it gains control of a given system. Notably, Win32/Kasidet, malware used to conduct DDoS attacks also known as Neutrino bot, and Win32/Lethic, a well-known spambot, are regularly dropped by Dorkbot onto compromised systems.
Win32/Dorkbot has been around in different forms for several years now and is still very prevalent. As we still see thousands of detections every week coming from most parts of the world and fresh samples arrive daily, it seemed like a suitable target for a disruption effort. If you believe your system might be infected by Dorkbot, please run our free tool to clean your system.
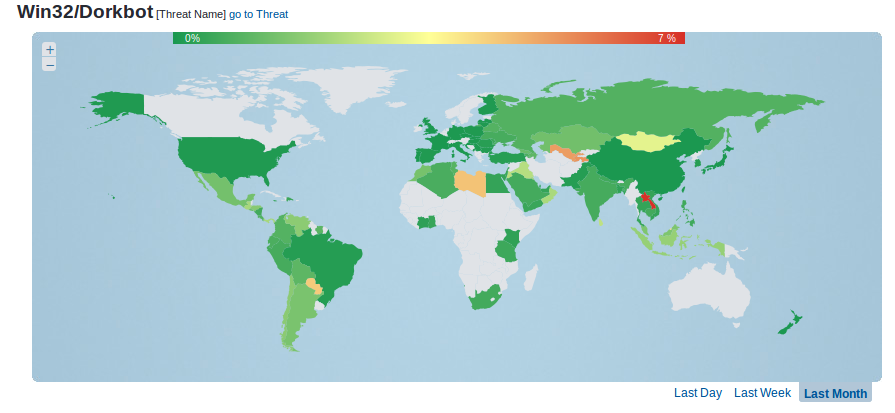
Figure 1 - Win32/Dorkbot is malware that has been around for quite some years now and is still affecting a large number of systems
Figure 1 Win32/Dorkbot is malware that has been around for quite some years now and is still affecting a large number of systems.
A modular design
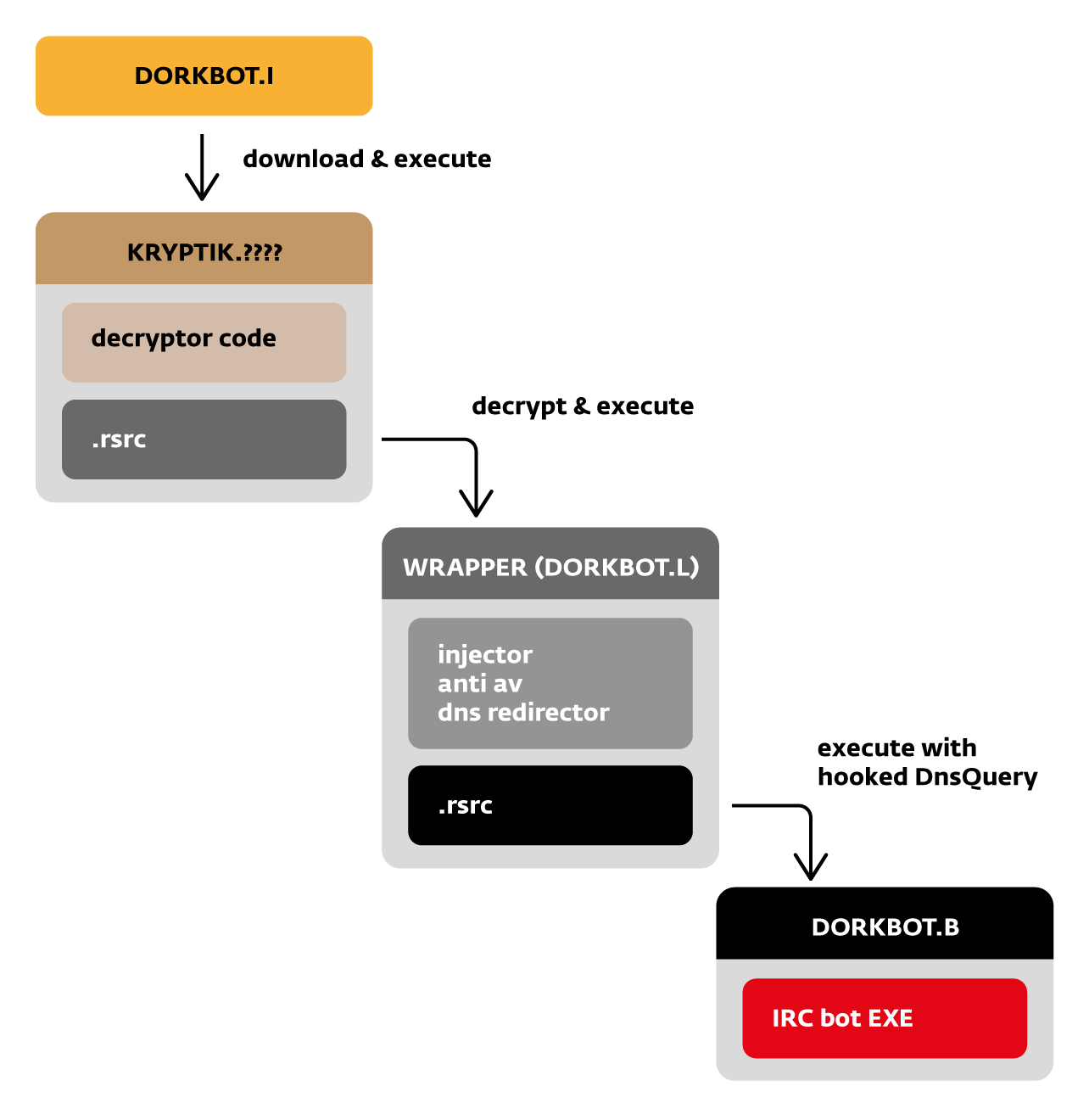
The following diagram explains better the different modules that make up the latest versions of Dorkbot samples we analyzed. This will also help researchers better understand the naming we use for variants of this threat.
Let’s take a typical infection scenario to better illustrate the role of each module, specifically when a user gets infected by launching a Dorkbot sample located on a USB stick. Since Dorkbot is looking for removable media present on an infected system to use in order to replicate itself, many of our detections come from Dorkbot samples located on removable devices. Two types of files are found on removable media inserted in a system infected by Dorkbot: a dropper and .LNK files with enticing names that point to it.
So, to go back to our example, when the user launches the dropper – detected by ESET as Win32/Dorkbot.I – from the USB stick, it will first try to download Dorkbot's main component by contacting a hardcoded C&C server. The downloaded package is a heavily packed file that will ultimately decrypt and execute Win32/Dorkbot.L, a wrapper used to install the main component.
As can be seen in the figure above, it will launch the main Dorkbot IRC component, detected by ESET as Win32/Dorkbot.B, and will hook the DnsQuery API while doing so. This is necessary because the main component does not contain the true C&C domains. In fact, when the IRC component tries to resolve these domains through the hooked API, the wrapper will instead try to resolve one of the many domains it contains. This convoluted process makes it harder to obtain the real C&C addresses.
Once the installation is completed, the system will try to connect to the IRC server, will join a specific channel and will wait for commands issued by the botmaster. Usually, the bot will soon receive commands to download and execute additional malware as described above.
Closing remarks …
Dorkbot is an old botnet that has been reinventing itself through the years. Its command and control infrastructure is one of the many that ESET tracks. This information is vital in order to keep track of changes in malware behavior and to be able to provide actionable data to help with disruption and takedown efforts.
Dorkbot uses old tricks to compromise new systems. Users should be cautious when opening files on removable media, as well as files they receive through email or social media. If you believe that you are infected with Dorkbot, we have a free tool for you. ESET products currently detect thousands of variations of Dorkbot modules along with the different malware distributed by the Dorkbot botnets.
Special thanks to Juraj Jánošík, Viktor Lucza, Filip Mazán, Pablo Ramos and Richard Vida for their help in this research.
Appendix A
Example of URLs targeted by Dorkbot password stealer:
*paypal.*
*google.*
*aol.*
*screenname.aol.*
*bigstring.*
*fastmail.*
*gmx.*
*login.live.*
*login.yahoo.*
*facebook.*
*hackforums.*
*steampowered*
*no-ip*
*dyndns*
*runescape*
*.moneybookers.*
*twitter.com/sessions*
*secure.logmein.*
*officebanking.cl/*
*signin.ebay*
*depositfiles.*
*megaupload.*
*sendspace.com/login*
*mediafire.com/*
*freakshare.com/login*
*netload.in/index*
*4shared.com/login*
*hotfile.com/login*
*fileserv.com/login*
*uploading.com/*
*uploaded.to/*
*filesonic.com/*
*oron.com/login*
*what.cd/login*
*letitbit.net*
*sms4file.com/*
*vip-file.com/*
*torrentleech.org/*
*thepiratebay.org/login*
*netflix.com/*
*alertpay.com/login*
*godaddy.com/login*
*namecheap.com/*
*moniker.com/*
*1and1.com/xml/config*
*enom.com/login*
*dotster.com/*
*webnames.ru/*
*:2082/login* (possibly targeting cpanel)
*:2083/login* (possibly targeting cpanel)
*:2086/login* (possibly targeting GNUnet)
*whcms*
*:2222/CMD_LOGIN* (possibly targeting DirectAdmin)
*bcointernacional*
*members.brazzers.com*
*youporn.*
*members*
Indicators of Compromise
| IoC | Hash |
| Win32/Dorkbot.I SHA1 | 820B3E3726026AD973EA8AD4B2FE5A9CCC710C6C |
| Win32/Dorkbot.B SHA1 | BA2AB99250B21E24258D0CFC30AC7DA058539A71 |