As regular readers of We Live Security will know, every December the ESET researchers put together their trends and predictions for cybercrime attacks for the coming year, availabe in our white paper section in We Live Securtiy. Last year, the emphasis was on internet privacy, a new assault on Androids, and a new wave of hi-tech malware; most of these issues have indeed appeared in blog posts during 2014. Today we offer a summary of the most important trends for 2015. In a few days, you will be able to download the full paper, with much more information plus numbers and graphs about our predictions: please stay tuned.
Targeted attacks
If there is one lesson we have learned in recent years, it is that targeted attacks are a rising trend, and next year won’t be an exception. Most commonly known as Advanced Persistent Threats (APTs), their main differences from traditional cyber-attacks are target selection, plus silence and duration of attack. First of all, in most of these attacks there is a selected target, as opposed to traditional attacks that use any available corporate targets for their purposes. Secondly, these kinds of attacks try to stay unnoticed for longer periods of time. In this context, it is important to note that the attack vector is often targeted social engineering techniques or 0-day exploits.
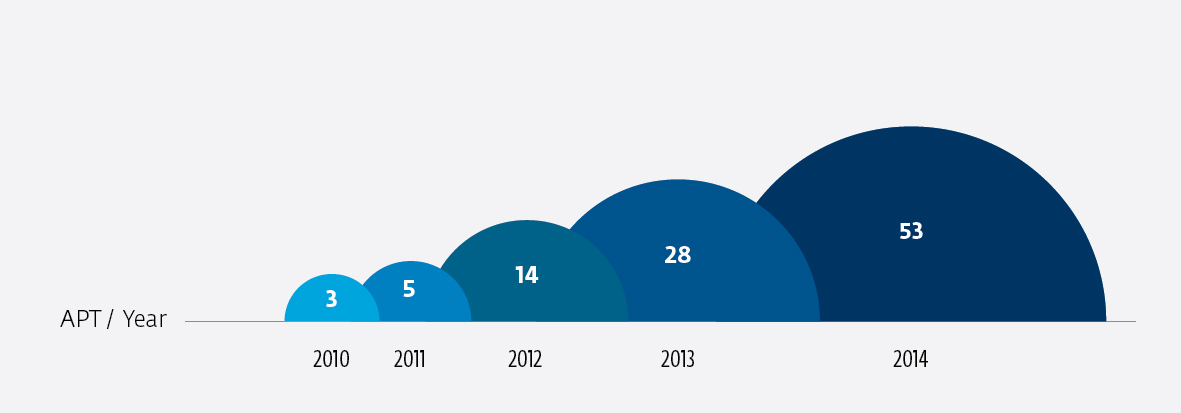
According to APTnotes repository (a site that collects APT attacks from various publicly-available documents and notes, sorted by year) these kinds of attacks have grown over the past several years from 3 identified attacks in 2010 to 53 known attacks in 2014 and probably many others as yet undiscovered. During 2014 we have published here in We Live Security some examples of these attacks, like the new BlackEnergy campaign or the Windigo Operation.
According a report from the United States Identity Theft Resource Center there have been 720 major data breaches during 2014, with 304 of them affecting the health industry (42.2%):
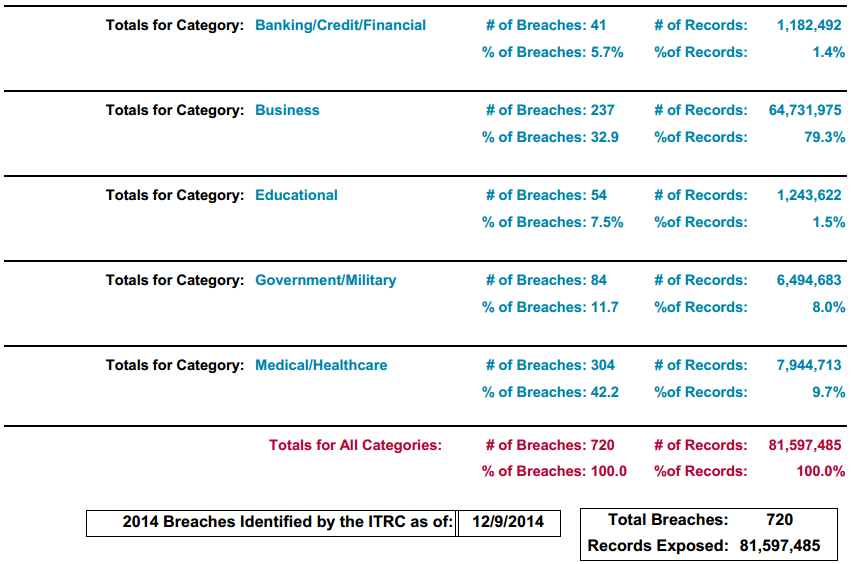
These stats are based on well-known public attacks, so it is reasonable to think that the statistics showing a growing trend is real; the true number, however, is probably bigger, taking into account attacks that never reach the public record because of confidentiality reasons.
Payment systems in the spotlight
In parallel with the growing use of online payment systems, the cybercrime interest in attacking them grows too. At this point, it is already obvious that cybercriminals will continue putting efforts into payment systems as more money circulates on the web. In 2014 alone, we have seen attacks like the one that affected some Dogevault users in May, when some users reported withdrawals just before the site was taken down. Apparently, the funds were in another wallet that contains more than a hundred million Dogecoins, an online currency.
On the other hand, traditional point of sale systems are still widely used and malware authors are well aware of that. In mid-2014 we published a blog post on We Live Security about the worm Win32/BrutPOS that tries to brute-force its way into PoS machines by trying a variety of (overused) passwords in order to log in via Remote Desktop Protocol (RDP).
There are other malware families for POS like JacksPos or Dexter, which could be responsible for big attacks such as Target (data on 40 million cards exposed), or The Home Depot, where 56 million cards were exposed during more than five months of attack (it started in April but was not discovered until almost September, when the company announced the leak).
It is interesting to note that since the BlackPOS source code was leaked in 2012, it will probably facilitate the creation of new variants of this threat that will increase over the next few years.
Bitcoins, ransomware and malware
In line with the previous trend, malware developers will continue putting efforts into online currency and payments systems during 2015.
For example, in the largest known operation of its type to date, a hacker reportedly harvested over $600,000 in digital currency earlier this year using a network of compromised machines. Through infected NAS devices the attacker created a folder named “PWNED” where a program called CPUMiner is stored that can be used to mine Bitcoins and also Dogecoins. Interesting note: this kind of attack creates new money instead of stealing it from compromised users, a brand new way of stealing.
Similarly, the SecureMac site also reported in February a Bitcoin miner that affects Mac OS users. The attacks spreads as a Bitcoin App, a legitimate app recompiled to contain a Trojan.
Finally, ransomware will be a key strategy for malware developers and it will be a more relevant threat in coming years. During 2014, we have seen big companies hit by ransomware (like Yahoo, Match and AOL). In July, ESET researchers published their Android/Simplocker analysis, revealing the first Android file-encrypting TOR-enabled ransomware. In December, in a panel discussion at Georgetown Law called “Cybercrime 2020: The Future of Online Crime and Investigations” it was said that “ransomware is the future of consumer cybercrime”.
Internet of Things -> Attacks on Things
Whole new categories of digital device are getting connected to the Internet, from domestic appliances to home security and climate control, and this trend has been dubbed the Internet of Things or IoT. The trend will accelerate in 2015 but sadly we see no reason why these things won't become a target for cybercrime. During this year we have seen some evidence of this emerging trend, like attacks on cars shown at Defcon conference using ECU devices or the Tesla car that was hacked to open doors while in motion, as discovered by Nitesh Dhanjani. Attacks and proofs of concept were shown attacking several SMART TVs, Boxee TV devices, biometric systems on smartphones, routers and also Google glasses!
It has to be said that some reporting on IoT hacking has exaggerated the scale of the problem. We mentioned this trend last because, while it probably won’t be a massive problem next year, it is an emerging space for cyber crime. We expect it will take a few more years until it is widely targeted. Nevertheless, this will be a trend, not for its quantity but for its uniqueness and innovation.
Conclusion
These are only the most important topics we have identified as big trends for 2015 in the world of malware and cyber-attacks. There are other current trends like mobile attacks that will continue to rise and much more information to be shared from us. Please stay tuned to We Live Security: the full paper is already available with a detailed analysis of each trend.
Thanks to the ESET LATAM Research Team's work on this article!



