The FBI made big headlines yesterday with its announcement of a high profile malware takedown related to a RAT called Blackshades (of which more in a moment). Hopefully this move, involving 97 arrests in 16 countries, will discourage the use of spyware by criminals. RAT stands for remote access tool and Blackshades is not unlike the DarkComet RAT that I wrote about in 2012. You can see DarkComet accessing a webcam in the illustration above, with a big hat tip to my colleague Cameron Camp, whose hand that is, captured during a live demonstration of how to defeat hacking tools during Interop Las Vegas in 2012.
[Note: All ESET products protect against Blackshades, detected as Win32/VB.NXB since February 2009, and also as Win32/AutoRun.VB.ANQ since October 2011. See “What is BlackShades and does ESET protect me from it?” in the ESET Knowledgebase.]
Bad RAT, good RAT?
Nobody wants a stranger spying on them, particularly when that spying includes surreptitiously watching them via their own web camera, hence the immediate public applause for this FBI operation. There were also cheers from people like myself and my colleagues in the security industry who are dedicated to keeping spyware and other malicious code off computers, including tablets and smartphones.
However, we do need to be careful when we talk about remote access tools as malware as they are a classic case of malice being in the intent of the user. Spying on an innocent person by sneaking a remote access tool onto their computers is clearly a malicious act, not to mention uber-creepy and generally despicable. Used for this purpose, a remote access tool is malware. But there are also positive and legitimate uses for remote access tools, such as remote computer support. And of course, a lot of spyware used by both state and non-state actors falls into the RAT category (part of a class of code that I like to call "righteous malware" because those who use it believe they are right to do so, whereas the owners of computers onto which it is secretly placed tend to see it differently).
Many RAT packages have appeared over the years and been put to use by criminals, but they are not all treated the same way, as my colleague David Harley points out: "There’s a difference here between BlackShades and more ‘professional’ malware like Zeus and Citadel. Its users constituted a relatively easy target by operating within an area seen as legally ‘grey’. Apparently, some of those involved were often less scrupulous about covering their tracks and their malicious intent than the career criminals associated with more heavyweight malware." One indication of this says Harley: "There was an awful lot of chatter about Blackshades on forums, whereas conversations about more sophisticated tools used for criminal activity tended to be far more discreet."
The implications? I think people pushing Blackshades might have been an easier target for law enforcement than some other players. However, I don't think there's any call for headlines like the one used by the Daily Beast ("FBI’s Huge Hacker Bust Could Be Bogus"). That said, Quinn Norton's article does raise some important points about RAT deployments in conflict zones, citing Morgan Marquis-Boire and Seth Hardy of Citizen Lab in Toronto who, along with the EFF, reported that Blackshades was used by the Syrian government to target anti-government activists (research article is here in PDF and EFF article, with Eva Galperin, is here). Norton also makes the very important point that, in terms of criminality, using a RAT for malicious purposes is way different from simply possessing it.
Maintaining perspective
I am firmly on the record when it comes to applauding law enforcement efforts to stem illegal abuse of computers and information systems, and I have previously predicted that such efforts will be stepped up (although that article from 2012 was as much wishful thinking as prediction). However, given limited law enforcement resources, it is vital that the right criminals are targeted. I'm not sure that the creators of Blackshades are as much criminals as the folks who broke into Target and stole tens of millions of credit card records. And there are clearly some non-criminals among those who purchased, acquired, or simply possessed the Blackshades codes. I hope to see prosecutions proceed with these distinctions in mind.
Where I do think we could see a welcome effect from the FBI Blackshades crackdown is at the margins and in the markets, discouraging those who are currently contemplating cybercrime or dabbling in the purchase of cybercrime tools on the underground markets. Seriously people, there are some very cool and potentially lucrative things you can do with coding and network skills that don't involve serious risk of a heavy knock on your front door,
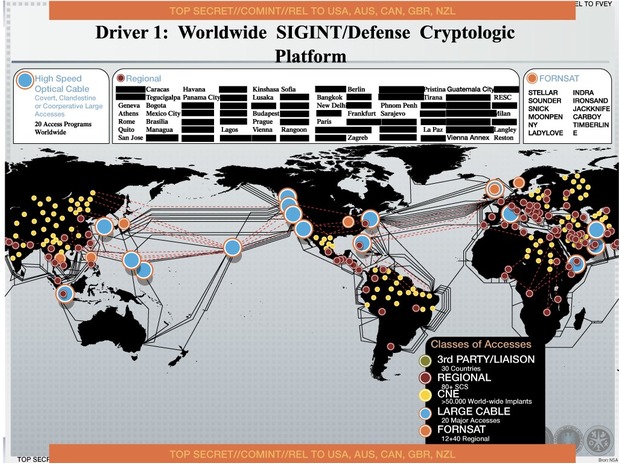
Finally, it is clear that public needs to do its homework to fully understand stories like these. After all, the FBI itself has been using surreptitious access to webcams to pursue criminals and terrorists "for years" using remote access tools. And this Powerpoint slide from "No Place to Hide", Glenn Greenwald's bestseller about the Snowden revelations, purportedly shows the NSA's efforts to "implant" malware on some 50,000 computers. Malware that would probably fall into the RAT category of "righteous malware".