Have you been wondering what trends in security and privacy ESET researchers are predicting for 2014? The following is a sampling, a year-end snack plate if you will. (Later in the month we will also be serving a main course of 2014 predictions in the form of a whitepaper from our colleagues in Latin America.)
Perennial readers of the ESET blog will know researchers do not relish making predictions, and yet each year we make them. Why? Because some people ask nicely, and because there is some practical value in looking ahead at where future attacks on information systems might come from, and in what form. Sometimes we name trends that are already in motion, like Bring Your Own Device, which has been a trend for several years. But we only draw attention to an ongoing trend if we think its persistence has implications for security and privacy (for example, one of researchers sees the increasing diversity of cheap smartphones adding to the BYOD challenge).
2014 predictions
First up is ESET Distinguished Researcher Aryeh Goretsky who predicts that, as locked-down computing environments such iOS and Windows RT come to the fore, we will see criminals increase their focus on identify theft. In other words: “Why 0wn the computer when you can 0wn the p3rs0n?”
Aryeh also observes that, while biometric authentication--such as a fingerprint reader--has largely been a feature of corporate computers: we now have the first widespread consumer computing device to incorporate this technology--the Apple iPhone 5s--and we will begin to see fingerprint sensors become increasingly common in other consumer computing devices. Aryeh suggests we will see this first at the higher “prosumer” end of the market, and then increasingly in less expensive devices, as the cost of sensors decreases. Low end devices will still probably not have these in 2014, partially because of cost and partially because of market segmentation reasons.
A third Goretsky prediction is that research into UEFI rootkits will continue, and we will probably see a handful of proof-of-concept demos, largely device or manufacturer-specific and due to flawed implementations of the standard or from improper key management by manufacturers. Or both.
Weighing in from the Netherlands, ESET Senior Research Fellow Righard Zwienenberg predicts the trend for Bitcoin to become more and more popular and valuable will continue. However, illicit Bitcoin-miners as well as Bitcon-stealers will also increase. Righard suggests that, as Bitcoins become more valuable, and because they are untraceable, operators of ransomware scams will increasingly demand payment in Bitcoin.
Righard also thinks 2014 will see a gradual increase in IPv6 installations along with the associated implementation faults that will allow some taking over of networks and systems.
A third Zwienenberg prediction is that the BYOD trend will get even larger due to more and cheaper (non)branded devices, making CYOD more needed than ever (see 'From BYOD to CYOD: Security issues with personal devices in the workplace'). Consequently, there will still be a big need to convince the people about the right device policies and security measures.
Weighing in from the redwood forests, ESET security researcher Cameron Camp predicts that the convergence of payment systems on smartphones and other mobile devices will increase the value of them as a target, and scammers will spend more effort aimed at financial fraud on these platforms.
Cameron also see nation states moving closer to drafting digital truces between trading partners in response to escalating tensions and the underlying need to continue strong trade in a semi-protected fashion. This is analogous to naval trade routes, where protecting cargo vessels carrying goods was deemed critical for semi-open worldwide trade, and therefore subject to various safe harbors, rules of engagement, etc.
Mr. Camp also predicts a year-long escalating cat-and-mouse game between anonymizing technologies (and related crypto products) and those who try to break into them in various fashions and with various motives. This will result in a bevy of new and novel technologies hitting the streets in an attempt to reclaim some modicum of the expectation of private communication, for better or worse (depending on one’s point of view).
ESET security researcher Lysa Myers sees the use of DDoS as a means of protest continuing to grow, particularly by people unhappy with the surveillance activities of governments and events in the Middle East. Indeed Lysa predicts a lot of hacking as well as DDoS for activist purposes in 2014; so, expect a lot of attacks against high profile, controversial targets, especially national and local governments and their infrastructure.
David Harley, ESET Senior Research Fellow, thinks cyber criminals will pay more attention to finding vulnerabilities and potential exploits in mobile operating systems. This will be driven, in part, by the convergence of payment systems on smartphones and other mobile devices that Cameron mentions.
Mr. Harley also thinks that, as the use of mobile devices--especially smartphones--as a means of strengthening privacy by two-factor authentication becomes more common, it will become more important to consider the use of other kinds of security software (where available) to reduce the risk of other attacks, including the interception of financial and other sensitive transactions.
Another Harley prediction is that post-Snowden concerns about whether providers are sharing cloud-stored data with government agencies--voluntarily or through enforcement of legal processes--will revive questions about the geographical location of data and cloud storage and processing. Older concerns about differing approaches to data privacy will flare up due to fresh mistrust and tensions between nations, not only between European and other nations, but even between European nations with differing views on how to counter terrorism without infringing on the privacy of their citizens. The General Data Protection Regulation, which among other things will aim to extend European Community data protection principles (see European Union Directive 95/46/EC) to countries outside the Community, is expected to be adopted in 2014. But it may not be compatible with sending data to be processed in countries where government rights to carry out surveillance are seen as excessive.
Finally, a few predictions of my own, starting with an educated guess about basic phishing attacks against consumers in developed countries. These will continue to be conducted from less developed countries where such activity is tolerated because it provides revenue to an under-employed citizenry.
A popular computer magazine asked ESET for one big and bold prediction for 2014 and my money is on: Cryptowar! An unprecedented level of interest in encryption products due to continuing revelations about state-sponsored surveillance of companies and consumers.
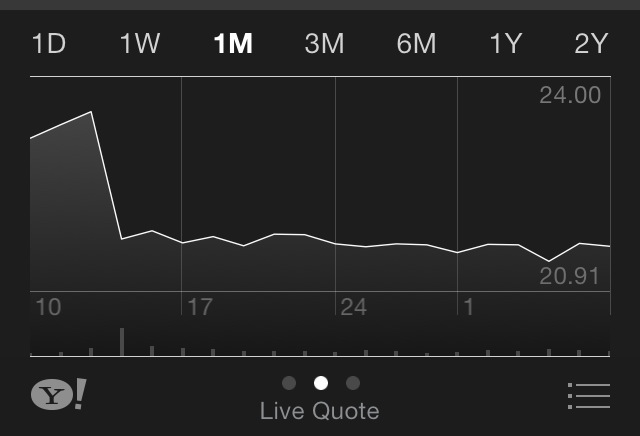
I will end this buffet of 2014 predictions with the first Internet fumble! I predict a small but not insignificant percentage of current Internet users in developed countries will scale back their online activities in light of continuing revelations about state-sponsored surveillance of companies and consumers. This and other aspects of the "Snowden effect" will not do the economy any good. I leave you with an illustration of what happened to Cisco's stock price after it publicly referenced the "NSA effect" on future sales.