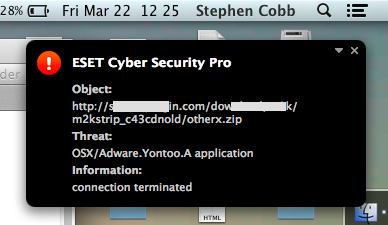
Mac users need to stay alert when clicking around for movie trailers because a well-tried malware ploy has been adapted from Windows to target Apple OS X, tricking users into downloading a new codec to watch a movie trailer. If you click Play on an infected website you will see something like this:
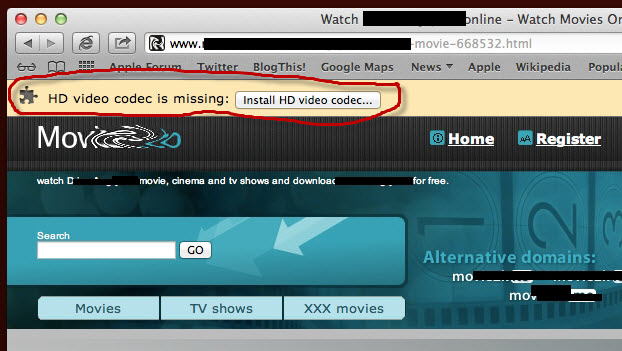
The user, eager to watch the video, is told that the HD video codec is missing, but all they need to do is click where it says "Install HD video codec." Do NOT do this! If you do, here is what comes next: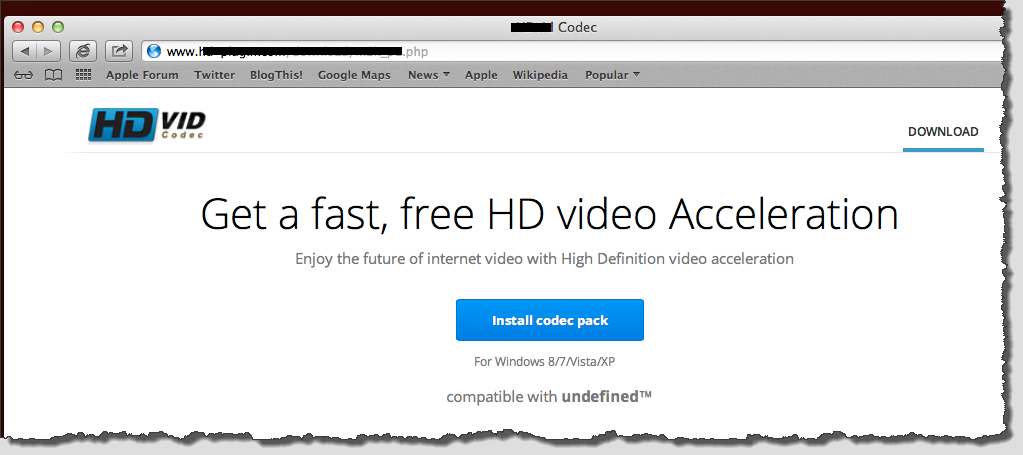
While there are some red flags here, like the trademark and the fact that it says Windows not OS X, it otherwise appears to be a legitimate page. Which is why some people have been clicking the Download link or the blue "Install codec pack" button. The end result is the unauthorized installation of a Web plug-in or extension called "Yontoo" that will run in the popular browsers on the Mac, like Safari, Chrome, and Firefox.
If you fall for this, a wealth of unwanted ads and redirections will likely follow, injected into pages on otherwise innocent sites. There are also reports of infection via phoney media players. The point is, criminals are using this plug-in to cheat online advertisers out of money by redirecting victims to sites that pay for traffic or clicks.
Protection and disinfection
If you are using ESET to protect your Mac, it will block this infection process, and it has been blocking it on Windows machines for some time (detected as OSX/Adware.Yontoo and Win32/Adware.Yontoo respectively).
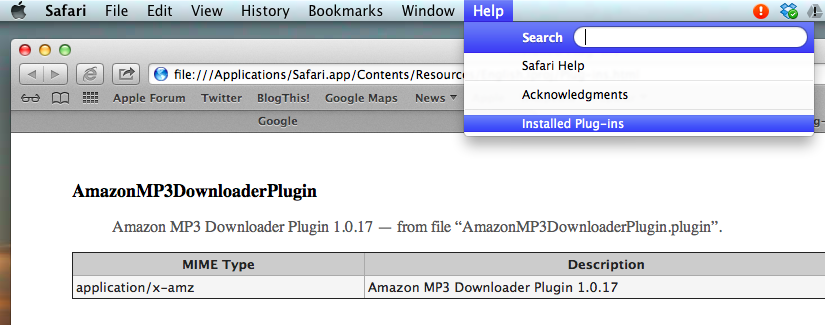
If you do get unwanted ads and think you might be affected, you can check your browser's plug-ins. For example, here's how you check via Safari:
You can use this list to find the actual file name of all plug-ins, for all browsers. For example, the Amazon MP3 Downloader that I use in Google Chrome on my Mac is the file AmazonMP3DownloaderPlugin.plugin. If I go to the Finder and delete that file from the Library > Internet Plug-ins folder on my hard drive, it will be removed from all browsers. The misbehaving plug-in files for "Yonto" that you want to remove are: Yontoo.safariextz, YontooFFClient.xpi and YontooLayers.crx.
Note that CNET is today reporting that Apple has released updated XProtect malware definitions to protect against this bogus Yontoo (identified as "OSX.AdPlugin.i").
What does this Mac malware mean?
An infection technique and criminal scheme that was previously found to be successful against Windows users is being tried against Mac users. Why? Economics. And while we cannot predict the future, we can predict the outcome of economic calculations. If there is a way to make money from attacking Macs, you can bet someone will try it. With the exception of malware designed for political or hobby-activist purposes, all malware development is driven by fairly straightforward risk-benefit, return-on-investment analysis. In other words, most malware campaigns are not mounted unless somebody thinks there is money to be made, with a low probability of getting caught.
Here's one way to look at what is going on here: Imagine you are an aspiring cyber-criminal. You want funding for your scam. You stand before a cigar-smoking Mr. Big in a dark and sinister office. You tell him the cost of adapting a proven Windows attack to target an alternative platform is relatively low. He gives you the okay for a trial run. You come back to him a few weeks later with statistical analysis showing that users on the alternative platform, in this case OS X, fall for the scam and the fraudulent fees thereby generated are substantial. Mr. Big gives you the greenlight for a full-scale campaign.
You don't need a vivid imagination to see the scenario repeating itself in the future.